Choosing the Right Compliance Framework for Your Business: NIST vs ISO
When it comes to data security and compliance, businesses need to follow guidelines and standards to ensure they are protecting their sensitive information and customer data. However, choosing the right compliance framework can be overwhelming, with many options available. NIST and ISO are two of the most popular and respected frameworks.
This blog will look closely at NIST vs ISO 27001 (the most recent addition to the ISO series) and help you determine which compliance framework best suits your business needs.
Whether you're a small business owner or an enterprise-level corporation, understanding the differences between these frameworks can help you decide to safeguard your organization against potential cyber threats and data breaches.
NIST Cybersecurity Framework: An Overview
The Cybersecurity Framework (CSF) was developed by the National Institute of Standards and Technology (NIST) in 2013.
It's been used for everything from nanotechnology to cybersecurity ever since, and it's a key resource for companies seeking to develop or improve their cybersecurity frameworks.
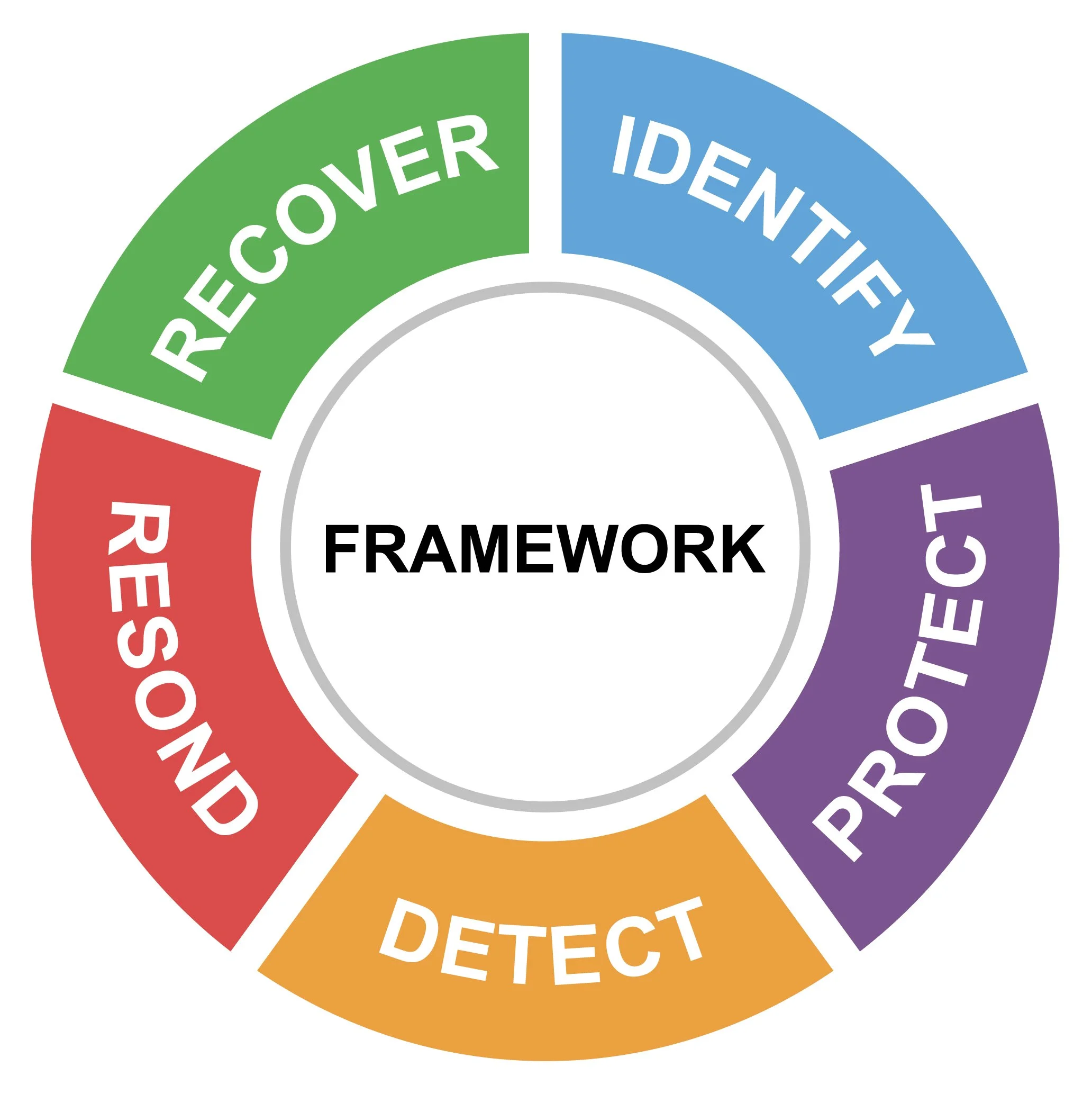
The NIST CSF is focused on 5 key areas:
Identify
Protect
Detect
Respond
Recover
The NIST Cybersecurity Framework is organized in a hierarchical fashion that allows organizations to begin with the lowest level of protection possible and then move up as needs change over time.
In addition to providing a path for organizations to improve their security posture, the NIST Cybersecurity Framework also offers resources that can be used by individual employees to help them understand how they can take steps toward greater security on their own time.
Read more about the history of the NIST Cybersecurity Framework (CSF)
Obama’s Cybersecurity Executive Order: What You Need to Know
Trump’s Cybersecurity Executive Order: 4 Things You Need to Know
How NIST CSF Is Used
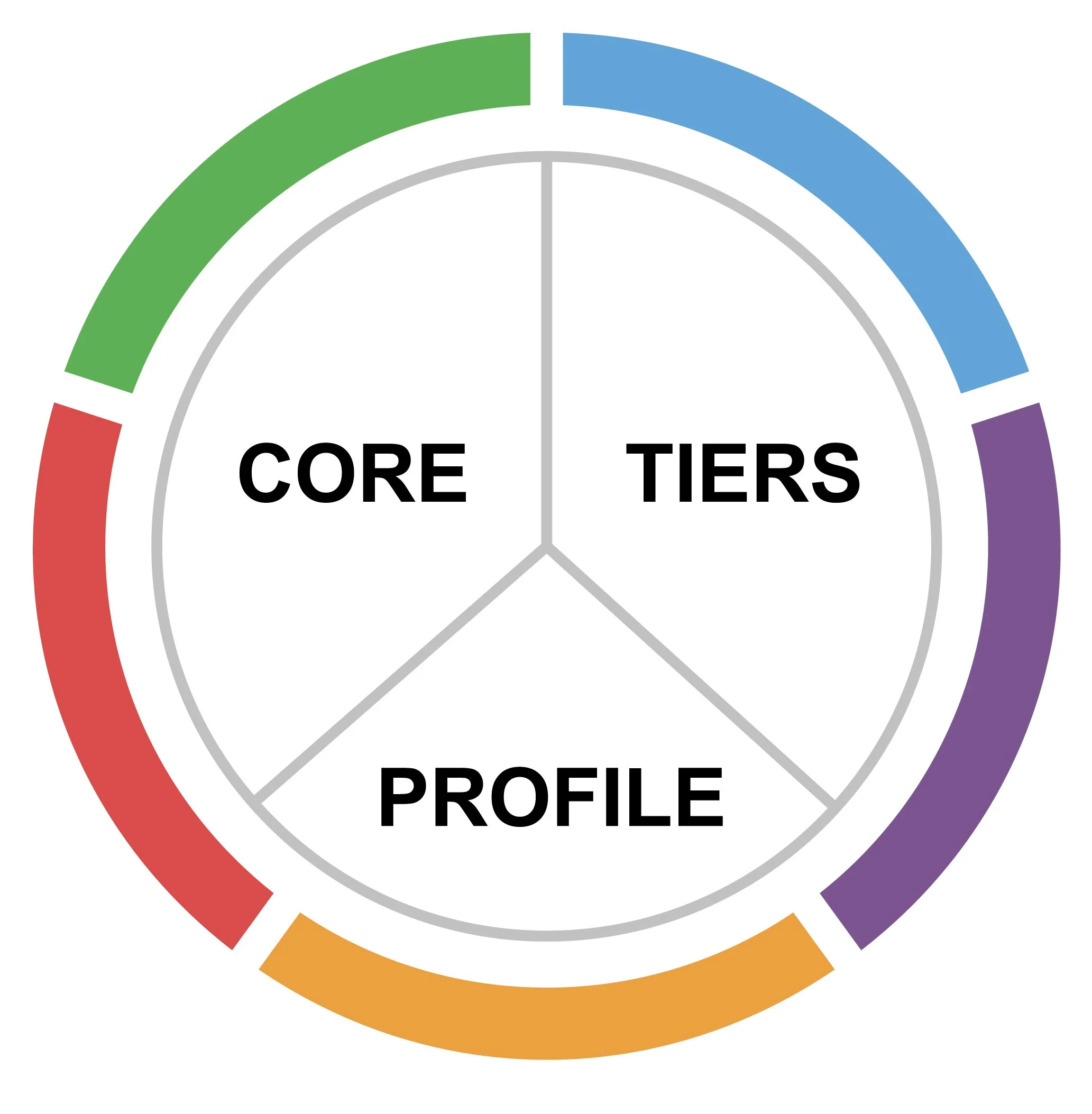
There are three major components to the system:
1) Framework Core:
This is the baseline of the NIST CSF and what everything else is built on. The five functions that make up this core mentioned previously ( Identify, Protect, Detect, Respond, and Recover) are used to identify and manage any risk management issues. The five core functions of cybersecurity contain 23 categories that provide the basic elements needed to establish a solid defensive strategy.
2) Implementation Tiers:
NIST CSF Tier levels provide benchmarks for organizations' cybersecurity efforts, with the highest tier (4) representing a strong adherence to the framework's rules and recommendations.
The four implementation tiers are:
Tier 1: Partial
Tier 2: Risk Informed
Tier 3: Repeatable
Tier 4: Adaptive
3) Profiles:
A profile at each tier allows you to gauge your current level of risk and see how improving your security measures can increase protection for everyone on the network.
When you have analyzed these three components, you can better understand the risk level of your system and identify any underlying problems. As such, you will be able to prioritize any issues and take action sooner rather than later.
Do you know how your cybersecurity defense efforts stack up against your competitors? Contact Johanson Group today to find out.
Now, before we get into NIST Cybersecurity Framework vs ISO 27001, here's a brief introduction to ISO 27001, so that you can better understand why it’s important for businesses looking to protect their data.
ISO 27001: An Overview
The ISO is an independent international body based in Geneva, Switzerland. It provides standards on a wide range of topics—including information security—to governments and businesses around the world.
First released in 2005, the 27000 standards are a family of corporate guidelines for information technology and security risk management.
ISO 27001 (aka ISO/IEC 27001:2013) is an information security risk management standard that specifies requirements for a comprehensive ISMS.
The basic goal of ISO 27001 protect your company and customer information with:
Confidentiality: Only authorized persons may access data.
Integrity: Only authorized individuals can modify the data.
Availability: The information must be retrievable by authorized persons whenever they need it.
ISO 27001 is a process standard that outlines the steps needed to develop and maintain an ISMS. However, it doesn't include specific language on performing these tasks; you need other resources like the NIST SP 800-30 for guidance on how exactly do them (but not included in ISO 27001).
Learn more about the history of security audits here.
How ISO 27001 Is Used
So how does ISO 27001 work?
The standards here are meant to help businesses systemize their cybersecurity, growing a system that was put into place to cover certain issues into a full IT management system. You can get certification for compliance with ISO 27001, whether that's through the ISO themselves or a third-party auditor.
With ISO 27001, the scope can be limited to just one aspect of the company, rather than the company as a whole. For example, you could get certified just for your data center, or just for your cloud-based data storage—or any other aspect of your information technology (IT) systems.
When getting certified, you'll have to go through two stages:
Stage 1: Documentation review: Where your documents on processes, policies, and procedures will be audited. They will be looked at to ensure that they meet ISO standards.
Stage 2: Certification Audit: This will involve an auditor doing a full and thorough on-site assessment to ensure that your systems comply with ISO 27001 fully.
Wondering What the Difference is Between SOC 2 and ISO 27001? Find out!
ISO 27001 vs. NIST CSF: Key Differences
Now that you know the basics of NIST CSF and ISO 27001, if you want to improve and certify your cybersecurity systems, which one should you follow? Both of them are highly useful, and it just depends on what you need from them as a company.
Here are some of the key differences between them:
Risk maturity
The age and sophistication of your business's security system will help you decide here.
If you're just getting started with a comprehensive security program, then the NIST Cybersecurity Framework is likely to be a better fit for your organization.
For those that have a more mature system in place and need certification, ISO 27001 is going to be the way to go. This is because it's better at helping businesses mitigate issues such as data breaches.
Certification
For a cybersecurity system to be certified, it must conform with the ISO 27001 framework.
It's a valuable investment to hire an experienced risk management CPA for ISO 27001 audit, obtain your compliance certification and show stakeholders that you're taking cybersecurity seriously. NIST CSF is not a certification—it sets standards but doesn’t certify organizations against them.
Cost
ISO 27001 is a more advanced standard, so it charges for its documentation and other materials. NIST can provide you with good starting points for implementing an information security system and will be free of charge.
ISO 27001 vs NIST CSF: Similarities
Both ISO 27001 and NIST CSF are security frameworks that help organizations identify and mitigate risks. They are similar in that they both have the following elements:
• Risk assessment
• Risk treatment plan
• Corrective actions for non-conformities discovered during risk assessments
• Continuous improvement processes
Both frameworks also require organizations to have a documented security policy, which is one of the first steps in implementing both standards. Additionally, both frameworks require that organizations develop a Security Awareness Training Program (SATP) to educate employees on their roles in information security.
Can NIST CSF and ISO 27001 be Used Together?
Although you may want to choose one or the other when it comes to frameworks, sometimes combining them can be a good idea. The trick is figuring out why you'd want do that in your particular case.
A lot of new companies begin with NIST, as it allows them to get up and running without incurring any costs. However, they should consider ISO 27001—it's an international standard that's widely recognized by businesses across the world.
If they decide to move on to ISO 27001 compliance, certification will be much easier as they'll have done most of the work during NIST CSF implementation.
While there are advantages to implementing either of these two solutions, you can also benefit by using them in combination. You'll need to evaluate your options carefully so that you get the best possible security for your business needs.
Protect Your Business: Get a Risk Advisory CPA for Compliance and Data Breach Prevention—Here’s Why
As the world increasingly relies on technology, data security has become a top concern for businesses of all sizes. This is particularly true for SaaS startups and organizations that rely on Information Security Management Systems (ISMS) to protect sensitive information.
One way to ensure the security of your organization's data is to hire an experienced risk advisory Certified Public Accountant (CPA) who can conduct an ISO 27001 audit or NIST framework assessment.
Here are some reasons why this investment is worth it for your business.
1. Expertise in ISMS implementation
Implementing an ISMS can be a complex process, and having an experienced CPA on your team can be a great asset.
These professionals have the knowledge and expertise to guide your organization through the implementation process, ensuring that your systems are set up correctly and are aligned with industry best practices.
An experienced CPA can help you identify potential risks and vulnerabilities and develop mitigation strategies.
2. Compliance with international standards
Since ISO 27001 is an international standard for information security management, and the NIST is a framework developed by the US government to help organizations manage and reduce cybersecurity risks, compliance with these standards is crucial for businesses that handle sensitive information.
A risk advisory CPA can help ensure compliance with the new standards, lowering your organization's risk of a data breach or cyber attack.
3. Protection against financial loss
A data breach or cyber attack can be costly for any business, particularly for startups just getting off the ground.
According to a study by IBM, the average cost of a data breach is $4.24 million. This cost includes legal fees, regulatory fines, and lost business.
By investing in an experienced risk advisory CPA, you can reduce the risk of a breach or attack, potentially saving your business millions of dollars in the long run.
4. Improved reputation
A data breach can damage your organization's reputation, causing customers to lose trust in your business. This can result in lost business, decreased revenue, and difficulty attracting new customers.
By investing in an experienced risk advisory CPA, you can demonstrate to your customers that you take data security seriously, improving your reputation and increasing customer trust.
Are you forgetting SOC 2? Don’t! As a SaaS organization SOC 2 Compliance is crucial— Read more
Conclusion
Choosing the right compliance framework for your business is a critical decision that can significantly impact your organization's data security and overall success.
Both NIST and ISO 27001 offer comprehensive guidelines and standards for information security and data privacy, and choosing one over the other depends on your unique business needs, industry regulations, and the level of security you require.
By assessing your business's specific risks and compliance requirements, you can select the most appropriate framework that aligns with your objectives, budget, and resources.
Whichever framework you choose, remember that compliance is an ongoing process, and you must regularly review and update your security measures to maintain your organization's data integrity and protect your customers' sensitive information.
Ready to Get Started?
Ready to take the first step in protecting your business against cyber threats and ensuring compliance with industry regulations?
Contact Johanson Group today to schedule a consultation with our expert risk advisory specialists. Our team has extensive experience in navigating the ISO 27001 audit and compliance process, making it seamless and understandable for businesses of all sizes.